iGrant.io Self-Sovereign Identity (SSI) Services describe the SSI enablers and tooling distributed by iGrant.io. The purpose is to make it easy for organisations new to SSI to adopt and implement Self-Sovereign Identity based on Decentralized Identifiers (DIDs) and Verifiable Credentials (VCs), a new digital identity standard.
iGrant.io SSI services are based on open-source Hyperledger Aries project, a Decentralized Technology (DLT). iGrant.io is primarily contributing to this via NGI-Trust eSSIF-Lab initiative, our open source code is hosted at Decentrialised Data Exchange GitHub. The source code is based on Apache 2.0 open source licensing. All efforts have been made to ensure that schemas etc. follow open standards.
The Aries playground environment, makes it easy for developers to issue Verifiable Credentials on behalf of an organisation (Data Source). These credentials can be used by individuals to prove their data to any Data Using Service.
Background
Before going into the details, it is important to understand what is meant by SSI and DLT. These are brief explanations, with links to details are provided.
Self Sovereign Identity (SSI)
Self-sovereign identity (SSI) is a term used to describe the digital movement that recognizes an individual should own and control their identity without the intervening administrative authorities. SSI allows people to interact in the digital world with the same freedom and capacity for trust as they do in the offline world. With SSI, the power to control personal data resides with the individual, and not an administrative third party granting or tracking access to these credentials. Definition comes from sovring What is self-sovereign identity?.
SSI principles fit well with GDPR regulation. These are the principles of Self-Sovereign Identity originally published by Christopher Allen in 2016 in The Path to Self-Sovereign Identity.
- Existence
- Control
- Access
- Transparency
- Persistence
- Portability
- Interoperability
- Consent
- Minimalization
- Protection
Distributed Ledger Technology (DLT)
To avoid lockin for a single solution provider (silo) and allow for interoperability between different actors in the personal data handling arena a distributed solution is required. A distributed ledger technology (DLT) based on blockchain allows establishing trust between actors and exchange of data. The exchange of data can be done securely and with zero knowledge proof. Zero knowledge proof limits private data shared by simply answering a claim. For example, I prove I am over 18 without revealing more personal information than is necessary like full date of birth. To test DLT refer to instructions in Aries play ground. This secure data exchange is accomplished by using verifiable credentials which captures the data that can be cryptographically verified. These verifiable credentials are kept in the individual's wallet and can be used as in the given exampe.
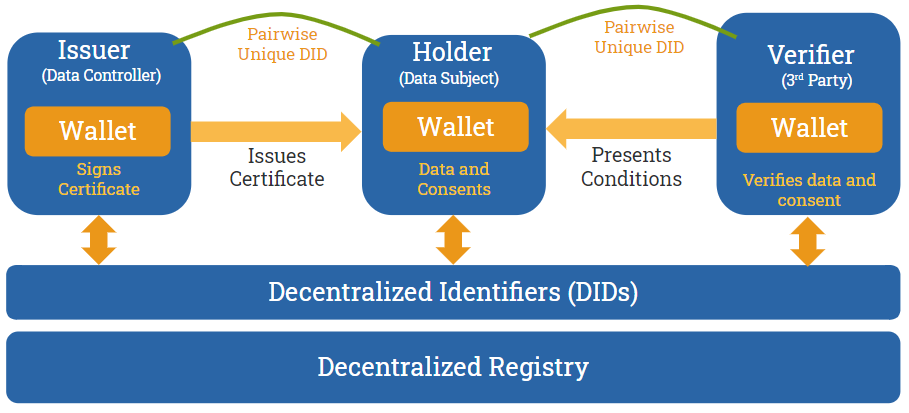
The communication is protected through the usage a DLT framework. Every new relationship is established by creating decentrlized identifiers that are unique for that communication. When the relation ends so does the decentralized identifiers.
Key features of SSI
The biggest challenge with handling personal data is how to make it safe and ethical without revealing more than what is necessary. The data exchange is prone for misuse, or worse no exchange at all which benefits the companies with the source data and stiffles competition.
The following are are the key reasons why it is necessary to deploy an SSI based solution to encourage a healthy and ethical data exchange.
Trusted communication
In SSI, trust the data sharing is done between clearly identified entities, be it between individual and businesses or between businesses. The default mode of communication is anonymous while providing an option to establish identity if needed.
No data leakage, limited to purpose
Frequently too much information is shared or leaked by giving full access to personal data rather than limited to purpose. By limiting the amount of information that is shared it becomes safer both for the individual, as well as, for the business receiving the information. The business can avoid having to handle extra personal information in case of data breaches may result in huge fines.
No forms, all digital
Sharing of personal data should be done digitally and can be done without requiring to fill out forms. Information can be automatically populated based on information individual already has in their possession or have ownership. To achieve this a presentation of a digitial wallet collects verifiable credentials that can be used to populate forms. The entries in the form are cryptopgraphically checked to ensure they are not modified through proof of claims.
No siloes, encourages reuse
Due to a standard format to collect data reuse is possible with higher level of quality. The individual has the control of their own data instead of being stuck behind siloes and can take advantage by a decentrlised solution provided by DLT.
Privacy risks
It is difficult to check that a business collecting personal information has applied due diligence and performed an assessment of the risks. Canada has put into effect the Privacy Act in which the risks has to be highlighted first when there is a higher consequence to the individual. The assessment and risks should be verifiable.
Conclusion
The next section SSI lifecycle provides the details of how the key benefits listed above are accomplished. At a high level this is accomplished by having a clear Agreement in place to establish the governance surrounding the individuals GDPR rights and purpose for collecting data, Personal Data embedded in a verifiable credential for safer personal data exchange and Assessment to identify the risks and regulation compliance.
The SSI Lifecycle in the next section describes how the above features are realiased in an SSI implementation.