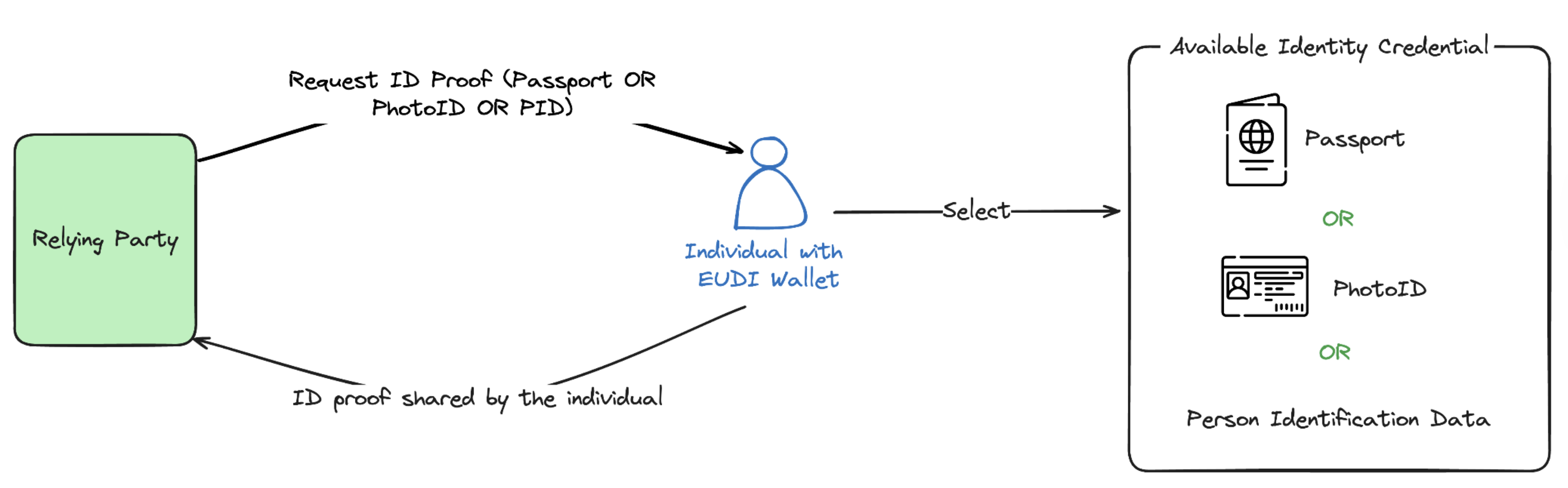
DCQL – Credential Set for proof of identity (Alternatives)
This workflow demonstrates a DCQL credential set for proof of identity using alternative credentials.
A verifier (Relying Party) wants to verify the identity of a holder and is willing to accept one of several alternative credentials:
- A
Passport - A
PID(Person Identification Data) - A
Photo ID
Using the Digital Credential Query Language (DCQL) with OpenID4VP and the Organisation Wallet Suite, the verifier can express this as a credential set: any one of these credentials is sufficient to satisfy the proof-of-identity requirement.
For the underlying DCQL query, diagram and example, see the “Credential set for proof of identity (alternatives)” use case in our DCQL concepts article.
Step 1: Get the API Key (Issuer Admin)
To obtain your API key, please contact [email protected]. Once you have received your API key, enter it in the field below and click the Set API Key button to save it for future use.
Step 2: Create Credential Definition (Issuer Admin)
To create a credential definition, run the JSON body using the Run button. Alternatively, you can manually copy the JSON and use it in the body of the API request available here.
Note: The
kidvalue is mandatory with trust anchorx509. To obtain thekidvalue for the respective organisation use the API Request available here.
From the API response, copy the credentialDefinitionId and id value from the credentialDefinitions array for use in the Step 3.
The issuer can define credential definitions for the following identity credentials:
Passportwith credential formatdc+sd-jwtPIDwith credential formatdc+sd-jwtPhoto IDwith credential formatmso_mdoc
Passport
The Passport credential is a digital representation of a physical passport, issued according to the EU Digital Travel Credential (DTC) specifications and International Civil Aviation Organization (ICAO) standards. As part of the EU Digital Identity framework, it allows holders to use their digital identity for secure border crossings and online identification by extracting verifiable data from the electronic Machine-Readable Travel Document (eMRTD).
Request
Response
PID
Person Identification Data (PID) is a standardized European identity credential defined under the EU Digital Identity Framework (eIDAS 2.0). It contains essential personal information including family name, given name, date of birth, and address, enabling secure digital identification across EU member states.
Request
Response
Photo ID
Photo ID is based on an electronic Machine-Readable Travel Document (eMRTD), is issued and verified as a digital credential under the EU Digital Travel Credential (DTC) framework and the EU Digital Identity Framework (eIDAS Regulation). For more technical details, please refer to EWC RFC 013: Issue Photo ID.
Request
Response
Step 3: Issue and Receive Credential (Issuer/Holder)
The holder of the wallet submits a request for the issuance of a credential by executing the JSON code block below using the Run button in InTime issuance mode. Choose the credential format and replace <credentialDefinitionId> and <id> with the actual values obtained from the previous step. Alternatively, you may use the API available here.
After receiving the response, toggle the button provided to dynamically generate a QR code. The EUDI Wallet/Holder can then accept the credential offer using the Data Wallet (or any other EU Digital Identity Wallet) by either scanning the QR code or directly accessing the credential offer on their mobile device, such as via a browser.
Passport
Request
Response
PID
Request
Response
Photo ID
Request
Response
To receive and accept the credential via API. First, use the credentialOffer to call the Receive Credential API. Once you have the response, copy the credentialId and provide it at Accept Credential API to accept the credential.
Step 4: Create Presentation Definition (Verifier Admin)
To create a presentation definition for requesting proof, you can run the code block below using the Run button. Alternatively, you can manually copy the code block and use it in the body of the API request provided here.
Note: The
kidvalue is mandatory with trust anchorx509. To obtain thekidvalue for the respective organisation use the API Request available here.
Request
Response
Once a presentation definition is created, the presentationDefinitionId can be reused to verify multiple credentials in Step 5.
Step 5: Create Verification Request (Verifier/Relying Party)
To create the verification request, execute the code block below using the Run button. Alternatively, you can manually copy the JSON and use it in the body of the API available here.
After receiving the response, toggle the button provided to dynamically generate a QR code. The EUDI Wallet/Holder can then accept the verification request using the Data Wallet (or any other EU Digital Identity Wallet) by either scanning the QR code or directly accessing the verification request on their mobile device, such as via a browser.
Request
Response
Users can copy the presentationExchangeId from the JSON response for use in Step 7 to read verification history.
Step 6: Send and Receive Verifiable Presentation (Holder)
The holder wallet accepts (consents) to send the requested credentials.
- Receive Verification:
- Use the
vpTokenQrCode(step 5) with the API available here to receive the verification. - Copy the
presentationIdfrom the JSON response received from Receive Verification for use in Step 6b.
- Use the
- Filter Verification:
- Use that
presentationIdwith the API available here to find matching credentials. - Save the
<id>and<credentialId>from the response.
- Use that
- Send Verification:
- Use the
presentationId,<id>and<credentialId>with the API available here to send the credentials to the verifier.
- Use the
Step 7: Send and Receive Verifiable Presentation (Verifier/Relying Party)
- The Verfier (Relying Party) receives the requested credentials and can verify it. They may read the received credential by executing the Read Verification History API.
- From the response received, the
vpTokenResponsecan be decoded using JWT Decoder. - From the decoded response, the
verifiableCredentialinside the 'vp' can be further decoded to view the received credentials.